Two-factor authorization or two-factor authentication (2FA) is becoming an important part of the digital security world. The system was created with the goal of preventing hackers from getting unauthorized access to sensitive information, and yet many people who would greatly benefit from it don't understand exactly how it works. This blog post looks at the various aspects of two-factor authorization and shows how it can keep your accounts secure.
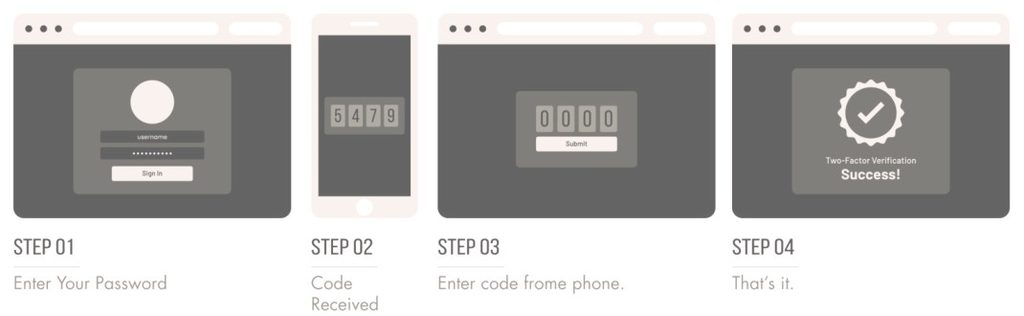
1. Two-factor authorization explained.
The past few years have seen a dramatic increase in the number of hacking and phishing attacks on various companies and people. The most common attack vector used by hackers these days is phishing, a social engineering scam where hackers send fraudulent email messages, trying to trick people into revealing sensitive information such as usernames and/or passwords.
2FA is a type of multi-factor authentication. It is commonly used as a security feature to verify the users' claimed identity by utilizing a combination of 'what the user knows' (e.g., username and password) and 'what the user has' (e.g., a one-time-password device, a smartphone that receives a unique code through an SMS, etc.). So, if someone steals your password, they're only halfway to gaining access to your account - they would also need to get access to your smartphone, for example. Two-factor authorization is a powerful way of confirming identity and ensuring that only the authorized user is allowed to access an account.
The security of the additional code depends on the strength of the algorithm used for generating the key, and the security of the web application. For most apps, the tokens are generated using the TOTP algorithm (Time-based One-Time Password). This algorithm combines the data provided by a shared secret key and the time read from the device to generate the passcode. Most apps change the codes every 30 seconds or so, thus preventing hackers from discovering them. Additionally, modern apps such as Google Authenticator use the Hash-based Message Authentication Code (HMAC) algorithm, which utilizes a secret cryptographic key, making it virtually impossible to guess the generated code.
2. Using the Google Authenticator app.
If you are a Google user, you probably have one or more Google apps, such as Gmail or Google Drive, already installed on your phone. To benefit from 2FA, you will need to install the Google Authenticator app manually, though.
The good news is that many large websites and platforms - Google itself, Dropbox, and Facebook, to name just a few - allow users to set up 2FA. If you've installed Google Authenticator, open it, and then scan the bar code that's displayed on the computer screen using your phone. Type in the 6-digit number below the bar code, click next, select your phone, and then you'll be set. Repeat the process for any website/platform that interests you.
That is all! From now on, when you open the Google Authenticator app, you will see a different one-time numerical code for any site that has been registered into the system.
3. Conclusion.
When it comes to protecting your sensitive data, poor security is always a major concern. While you must create and use strong passwords, you should also consider using a two-factor authorization system to protect your accounts. Hopefully, this blog post has helped you understand the basics of 2FA systems.
My recommendation is to start using two-factor authentication today; it is a great way of keeping your personal data safe by adding another layer of account security. I guarantee that with 2FA, you are going to be better protected against fraud, hacking and cyber crime.